Pyramid’s built-in multi-factor authentication (MFA) option adds a rock-solid layer of security to your BI application if your authentication provider does not offer it.
Passwords alone have proven to be an insufficient means of security in today’s world. More than 55 percent of enterprises use MFA to provide an additional layer of security. While some customers who have implemented Single-Sign-On (“SSO”) enterprise identity provider technologies (like SAML or OpenID) may have access to MFA from those systems, many customers who use other technologies like LDAP or Active Directory cannot access these capabilities. Pyramid’s built-in MFA framework with “Time-based One Time Passwords” allows customers to deploy and use MFA with the click of a button.
The Problem
Professionals are facing increasing security threats from tactics like phishing, pharming, and hacking. In response, enterprises now recognize the need to bolster their security.
Most hacking-related breaches are caused by stolen or weak passwords. Classic authentication requires a user login and password, but these are becoming easier to hack and steal. Furthermore, passwords are a headache to remember and change on an ongoing basis, so users often choose to reuse the same password between systems and devices. Consequently, a hack on one system may end up compromising many other systems.
The Solution
Multi-factor authentication (MFA) is a security protocol that requires multiple methods of authentication from independent categories of credentials to verify a user’s identity. Pyramid provides MFA where the user authenticates their credentials via Pyramid — this includes the internal authentication system, LDAP, or Active Directory.
Enrolled users are prompted to enter a machine-generated Time-base One Time Password (or “TOTP”) to log in, along with their username and password. This TOTP solution generates a unique code every 30 seconds using special authenticator applications (usually on the user’s mobile device) making it extremely difficult to circumnavigate. The authenticator apps, from vendors like Google or Microsoft, are usually free.
This ensures that even if a user’s credentials are stolen, access is blocked without the independent security code from the authenticator app. Administrators can enable MFA for the entire Pyramid deployment, or for each individual front-facing web server. Further, administrators can also reset the MFA token associated with a given user, ensuring that if the authenticator app is compromised, access can be centrally blocked.
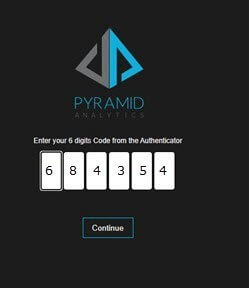
Example
The administrator sets up MFA in the web services panel, applying the authentication for all form-based logins into the platform.
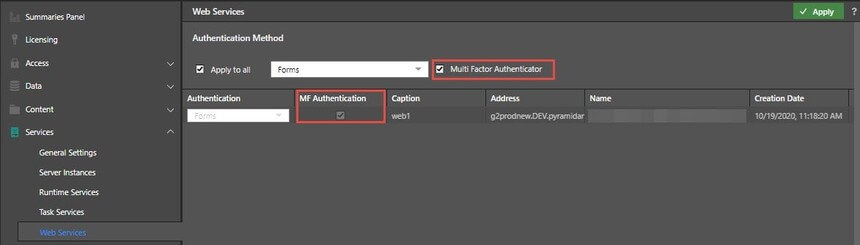
Users then log in. When they do, they must enroll themselves into the MFA by scanning the displayed QR code into their downloaded authenticator app. Once enrolled, the user is required to enter their username and password as normal and then supply their unique TOTP code, generated by the authenticator app, before gaining access to the system.
Summary
Passwords alone are an insufficient means of protection against security threats. Pyramid’s in-built multi-factor authentication safeguards your data environment with advanced security, without the hassle of using third-party tools or other applications.